Security
This section describes how to configure RegScale securely using defense-in-depth principles across multiple layers.
Security Configuration
This section describes how to configure RegScale securely using defense-in-depth principles across multiple layers.
1. Secrets
- Inject secrets using Kubernetes Secrets, environment variables, or a Key Vault available at container startup.
- Secrets entered in the RegScale Admin panel are encrypted at rest with AES-256, in addition to SQL Server encryption.
- Note: In self-hosted Enterprise deployments, RegScale does not store or access customer secrets. These are customer-managed and unrecoverable if lost. RegScale manages secrets only in its SaaS offering.
2. Database
- Enable full disk encryption for SQL Server.
- Use SSL/TLS to encrypt all SQL Server traffic.
- Configure and verify backups to support disaster recovery.
3. Encryption at Rest
- All files are encrypted at rest using the customer-defined AES-256 key.
- Files are MD5-hashed and blocked from download if tampered with outside the system (e.g., ransomware).
4. Encryption in Transit
- Customers must configure and maintain valid SSL certificates for all web traffic and API calls.
5. Security Scanning
- To support third-party security tools, navigate to:
https://yourdomain.com/login/scan
This disables the security banner for scanning access.
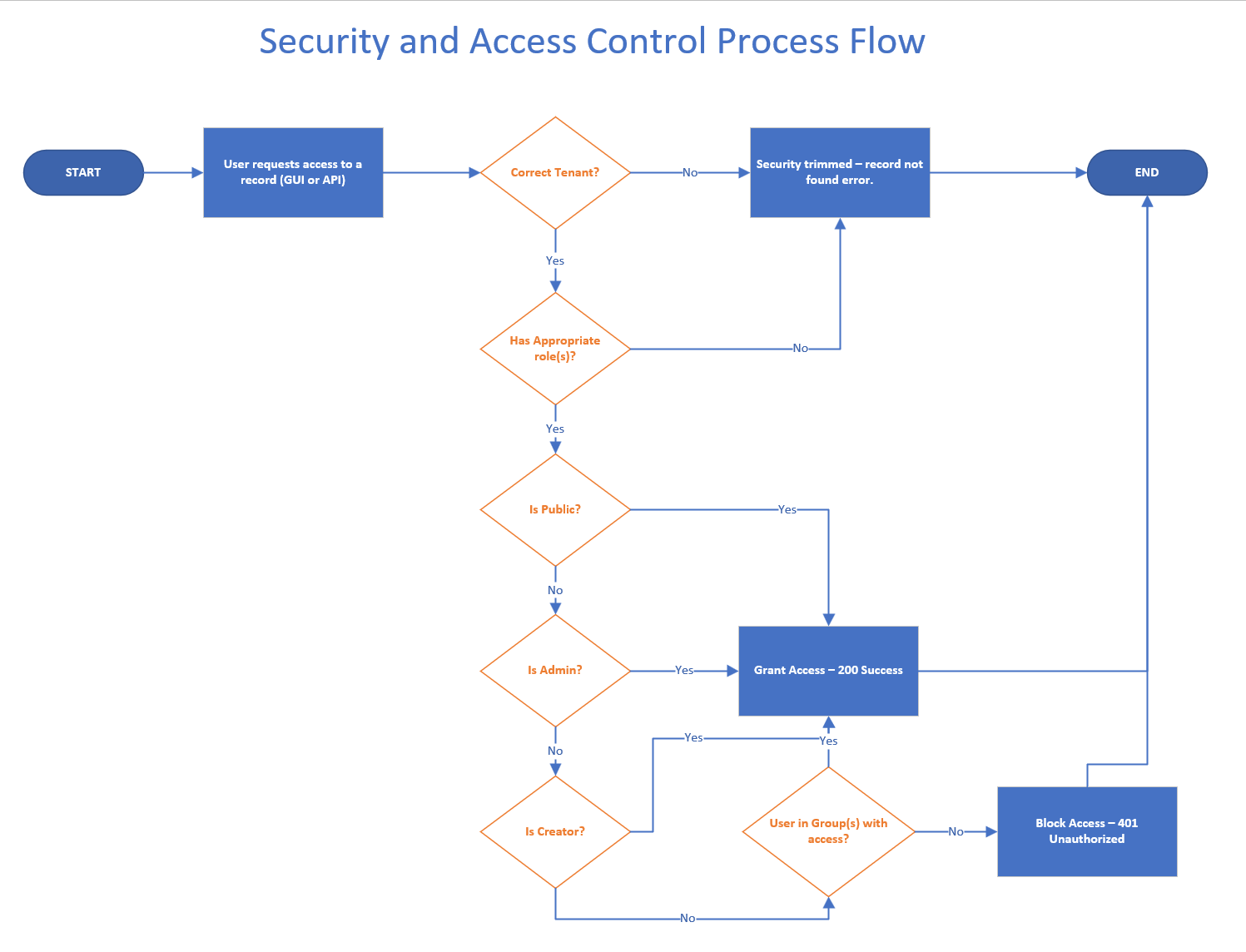
Layered Access Control
RegScale applies access control at three levels:
1. Tenant-Level Access
- RegScale is multi-tenant. Users are scoped to a single tenant and cannot access data outside their assigned tenant.
2. Role-Based Access
- User access is limited by roles aligned to the principle of least privilege.
For more information, see RegScale Users and Roles.
3. Record-Level Access
- Individual records can be restricted to specific groups.
- Groups can be granted Read/Write or Read-Only permissions.
The diagram below illustrates this access model:
Updated 11 months ago
