Building Security Plans and Conducting Assessments
Process Guide for Building Security Plans and Conducting Audits/Assessments
Author: J. Travis Howerton
Last Updated: October 1, 2022
The purpose of this guide is to provide step by step instructions and context around best practices for managing the overall Information Architecture within RegScale. While RegScale is a general compliance management system, it has rich features for automating complex compliance processes including building System Security Plans (SSPs), risk assessments, conducting audits, documenting issues (Plan of Actions and Milestones (POA&MS)), and developing corrective actions. This quick-start guide is designed to start a new customer from the point that RegScale is initially installed, to configuring it, to creating your first security plan and assessment plan/report.
This guide will provide context and process instructions for the following major areas:
- Understand the RegScale Information Architecture (using the Cyber Security use case)
- Building and Loading Your First Catalogues
- Create Security Profiles (sometimes called baselines or overlays)
- Building Security Plans
- Understanding Utilities
- Conducting Periodic Audits/Assessments
Before loading any data in the system, it is important to understand how data is logically related in the system and how the different modules interact with one another. The chart below shows the hierarchical relationship of the modules for a general cyber compliance workflow:
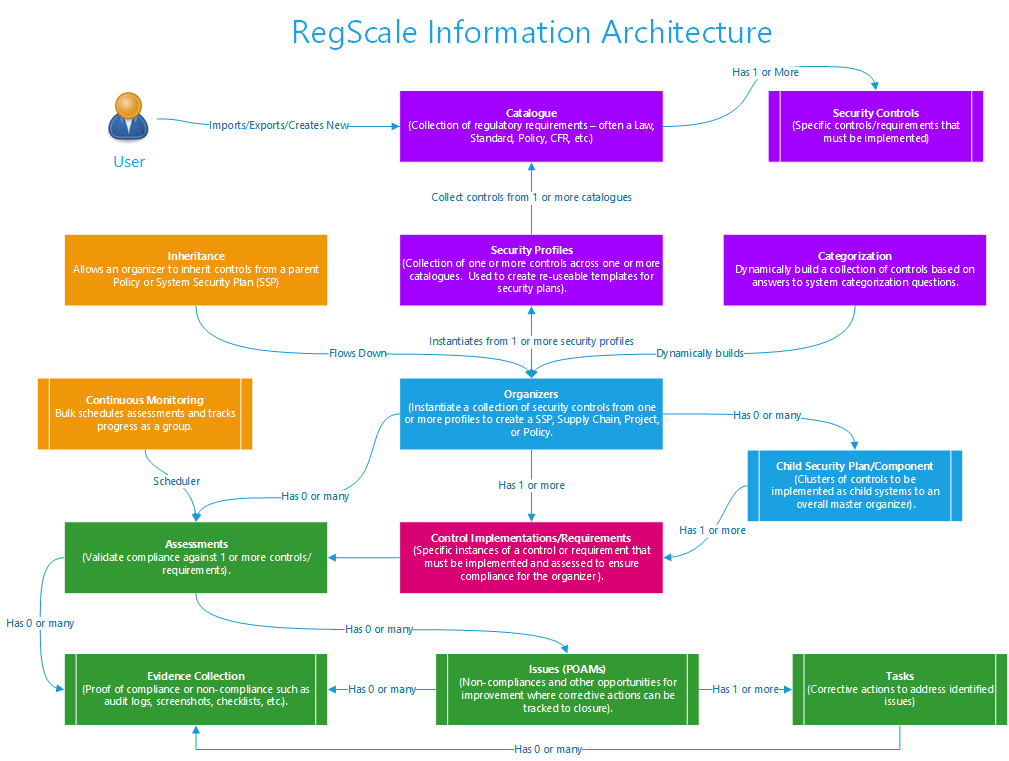
Each of these components is briefly explained below:
- Catalogues – a regulation or set of requirements that are published by regulators or international standards bodies that govern cyber compliance requirements. Examples include NIST, ISO 27001, or the Cloud Security Alliance (CSA).
- Security Controls – the collection of unique security controls/requirements that must be met to comply with the regulation. Each catalogue typically has many security controls.
- Security Profiles – collection of one or more security controls within one or more catalogues that form a baseline of requirements that must be implemented. Security profiles are templates that can be used to generate cookie cutter Security Plan formats (NOTE: They can also be applied to any Organizer module such as Projects, Policies, and Supply Chain Contracts/Vendors). In addition, security profiles can layer controls to have some addressed at a higher level (organizational or programmatic) while other controls are at a system level (IT system specific).
- Categorization - dynamic application of multiple profiles based on the answer to a collection of system categorization questions. This feature is more complicated than security profiles and is used for more sophisticated/layered use cases where one or more overlays may exist.
- Inheritance - allows you to flow down controls from another policy or security plan to support modern cloud inheritance use cases. This utility minimizes redundant work between systems.
- Security Plans – a system or logical boundary that defines a collection of assets or systems that will be managed as a logical unit for regulatory compliance purposes. Security Plans are created from security profiles or the categorization engine to ensure consistency and quality.
- Child Security Plans/Components – security plans can be “leveraged” in a parent child relationship where the child security plan inherits controls from the parent. This approach allows for controls to be implemented at the highest level where there is potential for re-use across systems while allowing control flexibility at the lower levels. This approach minimizes duplicate content and re-work versus traditional Security Plan processes. In addition, RegScale supports the Component concept which can be thought of as "Legos" for dynamically building a larger system based on its individual components or capabilities.
- Control Implementations/Requirements – each security plan has the controls from the profile instantiated as new control or requirement implementations. Under this architecture, one control in a catalogue could be implemented in many security systems. However, only one unique control can be implemented per any single Security Plan or Organizer module.
- Assessments – control implementations must be periodically audited and assessed as part of a continuous monitoring program.
- Continuous Monitoring - allows for bulk scheduling assessments as a group to support continuous monitoring programs.
- Issues (POAMs) – document deficiencies and non-compliances in the program at the overall system level or for a given control. When assessments fail and controls are not properly implemented, issues are used to document the non-compliance and to track efforts to remediate the deficiency or to accept mitigations to minimize the residual risk associated with the non-compliance.
- Tasks – document corrective actions to fix any issues identified. When issues are of a certain severity level, corrective actions may be required to address the issue and fix the root cause of the problem. Tasks allow RegScale users to assign work to fix specific issues. In addition, RegScale provides Kanban boards to drag and drop tasks as they are completed and move them across the board.
Now that each of the modules and their hierarchy are defined, the first step in configuring and loading RegScale is to identify the specific regulations that should be loaded as catalogues. The flow chart for managing catalogues is shown below:
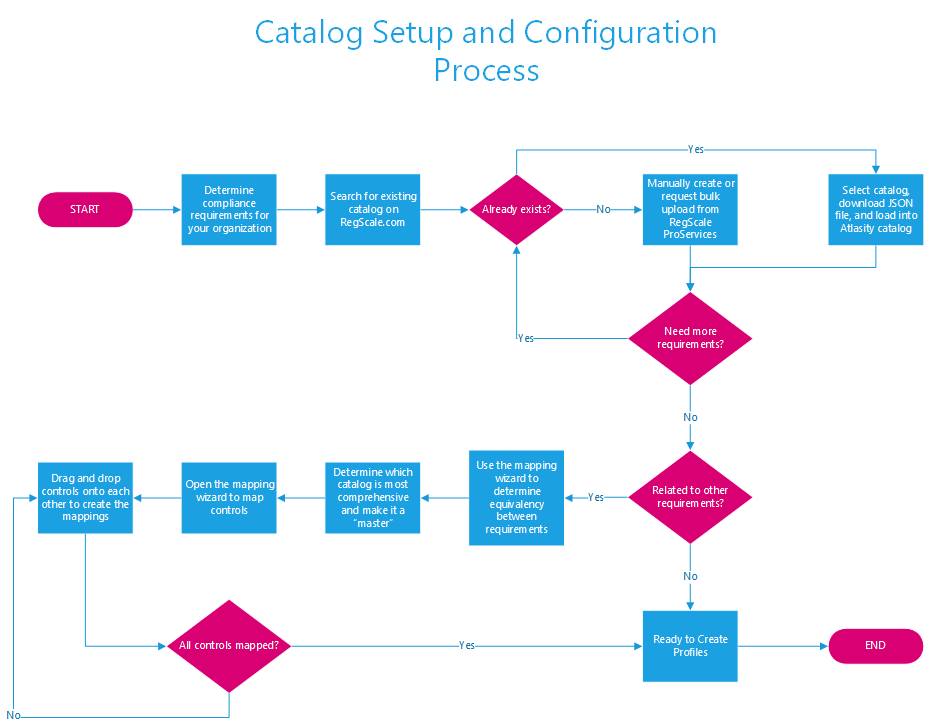
The process for managing catalogues is discussed below:
- Determine the requirements for compliance that your organization may be subject to by regulators. Examples might include:
- National Institutes of Standards and Technology (NIST)
- International Standards Organization (ISO)
- Cloud Security Alliance (CSA)
- Navigate to the RegScale site at https://www.regscale.com/regulations to browse the regulations supported.
- If the regulation already exists, download the JSON file and then load it as a catalogue in RegScale using the “Import” button. In the Compliance Cockpit, click the "Lightning" action button on the orange bar, then click the upload button to create the catalogue.
- If the regulation does not exist, there are two options:
- Manually load a new regulation and security controls by copying and pasting them into the RegScale user interface
- Automate the load using the RegScale Application Programming Interfaces (APIs). This can be done by:
- Developing custom scripts using APIs and CLI
- Contracting with RegScale or our system integration partners for professional services to digitize the requirements/controls (if a narrow industry standard or very specific to a given customer) – this is typically a paid ProServices engagement or bundled as part of an Enterprise Edition (EE) license purchase
- Requesting RegScale add the catalogue to its supported list (for a broadly adopted industry standard) – no cost option if accepted
- If more catalogues need to be loaded, go back to step 2 and continue the process until all are loaded.
- In many cases, requirements across catalogues may be similar or functionally equivalent. To save time and money in addressing these requirements, RegScale has a mapping wizard (our Transformer engine) to allow our customers to map security controls to one another.
- If controls across catalogues are functionally similar or equivalent, then:
- Determine the most comprehensive catalogue that should be used as the “master” to map all other requirements against.
- On the catalogue form, go to the Compliance Cockpit, click the Actions button in the orange bar (lightning symbol), and then click the “Mapping” button and select “Mapping Conversion” to make this catalogue the destination or master catalogue for all mappings.
- To begin mapping, go to the master catalogue, click the “Mappings” button and select “Mapping Wizard” and complete the following steps:
- Step 1: Pick the control to map in the master catalogue
- Step 2: Select the source catalogue to map its child controls to the master catalogue’s controls
- Step 3: Search for or select the appropriate control
- Step 4: Drag and drop the control onto the master control to create the mapping
- Step 5: Go back to Step 3 and continue this process until all controls are mapped to the master for this Source Catalogue
- If more catalogues need to be mapped, circle back to step 2 and select another source catalogue and repeat steps until all catalogues are mapped
- To view your progress at any time, click the green "Visualize" button to view the real-time grid showing the mappings
Once the catalogues are loaded and all mappings are in place, it is time to create profiles (NOTE: Mappings do not have to be done up front and could be added later if more convenient. If it will be done later, ensure that all profile generation is done from the master to ensure future mapping logic holds). The process for creating profiles is shown below:
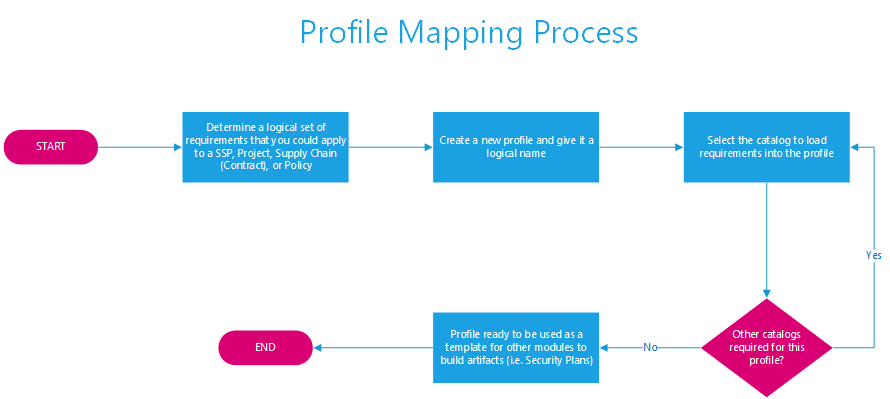
The steps for creating a profile (often called a baseline) are described in the steps below:
- Determine the requirements that should be logically organized to create a Security Plan. Profiles consist of one or more security controls in one or more catalogues.
- Go to the Security Profile form and create a new profile
- Save the Security Profile and complete the metadata
- After saving, go to the "Mappings" tab to add security controls to this profile
- Select the “+ Add Controls to Profile” button
- Select the Catalogue to map
- Select all of the controls from this catalogue to add to the profile (NOTE: There are options to easily add the whole catalogue or whole families of controls at once; you can also add individual controls one at a time)
- View the selected controls to confirm the appropriate controls are now in the profile (NOTE: selections will auto-save or remove as the checkboxes are clicked.)
- Save and exit the profile form
The last step in this process is creating a Security Plan and assessing its controls. This step is more tactical and allows for the creation of one-to-many discrete security plans that can model regulatory compliance for a system against a defined set of security controls that were established in the profile. An organization could have a single security plan defining all controls at the organizational level or a set of discrete security plans modeling individual and inter-related systems. Regardless of the granularity or fidelity of the Security Plan, the flow chart below shows the steps in creating a security plan and assessing its controls for compliance:
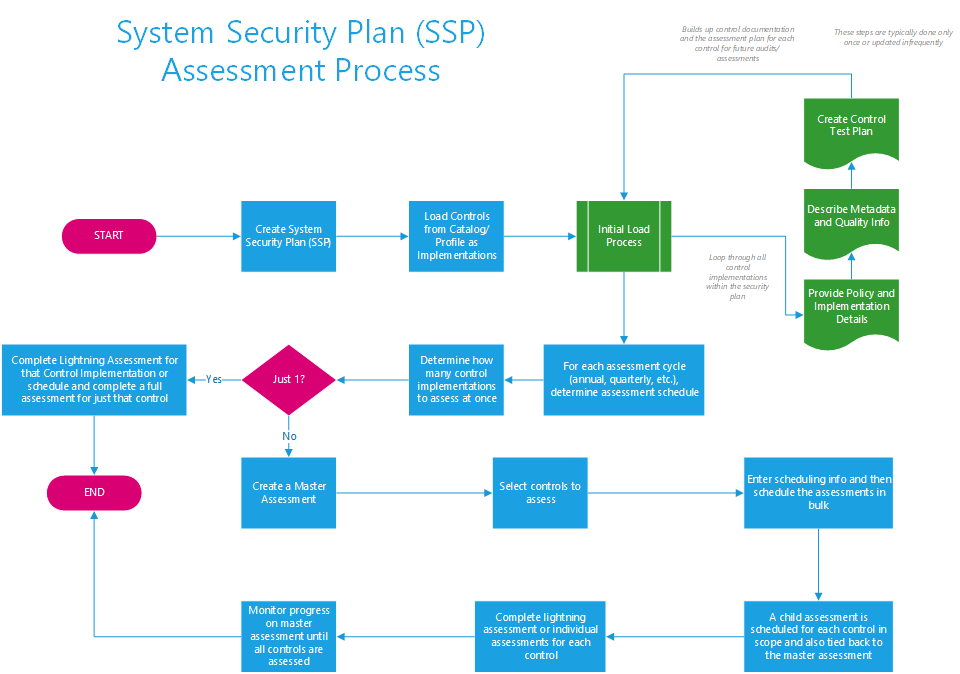
This process is further broken out as follows:
- The first step is to create a new security plan which consists of the following steps:
- Enter all required data about the security plan and save the record
- Use the security plan builder to add control implementations. The builder can be found in the orange Action bar of the Compliance Cockpit. These steps consist of:
- Open the Security Plan Builder after saving the Security Plan
- Read the instructions in step 1 of the wizard
- Apply the appropriate profile in Step 2 to load all of the applicable controls (NOTE: You can select multiple profiles and apply each of their controls to the plan in a “layered” manner)
- If necessary, manually add any additional controls to the plan
- Review the controls to be added in the “Preview.”
- If the controls are correct, click “Add Controls to Security Plan” in step 4 to complete the wizard and build the plan
- The page will refresh and show all controls now loaded in the Compliance Explorer
- In the compliance explorer, you then need to add the following information for each control implementation (NOTE: This is typically a one-time setup or at least infrequently changed):
- Enter the policy and implementation details for the control for this security plan
- Describe the related metadata and quality info for the implementation of the control
- If applicable, enter the test plan to validate compliance for this control which consists of adding one to many tests that must be satisfied for this control implementation and can later be used to conduct Lightning Assessments
- Once all control implementations have the data above established, the baseline is set for the security plan to conduct audits/assessments
- The next step is to determine the audit methodology. There are two common approaches that are used:
- Schedule and conduct one assessment at a time on a control basis to validate compliance.
- Bulk assessments – logically group many controls to be assessed at once as part of some sort of periodic audit/assessment (i.e., quarterly, annual, etc.)
- For bulk assessments, take the following steps:
- Create a new “Continuous Monitoring” assessment at the security plan level (available in the action bar of the Compliance Cockpit)
- Enter metadata around the assessment (i.e., when it should start, when it should end, etc.)
- Select the controls for this security plan that are in scope for this assessment
- Click the button to start the assessment which will:
- Schedule a new control assessment for each in scope control implementation
- Relate the assessment to the parent control implementation
- Relate the assessment to the Continuous Monitoring group
- Staff/personnel now complete the assigned assessments which are scheduled in bulk for convenience to the end user
- Staff/personnel track and complete their assessments via their workbench assignments (NOTE: Bulk assigned assessments are scheduled for the individual control owners)
- The system owner can track the status of the overall Continuous Monitoring group by reviewing percent complete information for all the controls in scope
- Once all controls are assessed, the Continuous Monitoring is complete
- The security plan owner can kick off Continuous Monitoring as often as they like and schedule multiple at the same time
- For bulk assessments, take the following steps:
RegScale provides an end-to-end user experience for determining requirements/controls, building security plans, and then assessing their compliance over time to provide continuous compliance in an efficient manner. From providing consistent templates, to establishing control policy and implementation information, to assessing and validating compliance, RegScale provides an end-to-end user experience that simplifies plan development, assessment, and reporting to generate efficiencies and improved customer satisfaction versus the traditional manual process driven by spreadsheets and word processing documents.
Updated about 2 years ago
