Implementing the RMF
Guide for Implementing the Risk Management Framework (RMF)
Author: J. Travis Howerton
Last Updated: January 31, 2022
The purpose of this guide is to assist RegScale customers in implementing the National Institute of Standards and Technology (NIST) Risk Management Framework (RMF) in our platform. The RMF provides a process that integrates security, privacy, and cyber supply chain risk management activities into the system development life cycle. The risk-based approach to control selection and specification considers effectiveness, efficiency, and constraints due to applicable laws, directives, Executive Orders, policies, standards, or regulations. Managing organizational risk is paramount to effective information security and privacy programs; the RMF approach can be applied to new and legacy systems, any type of system or technology (e.g., IoT, control systems), and within any type of organization regardless of size or sector.
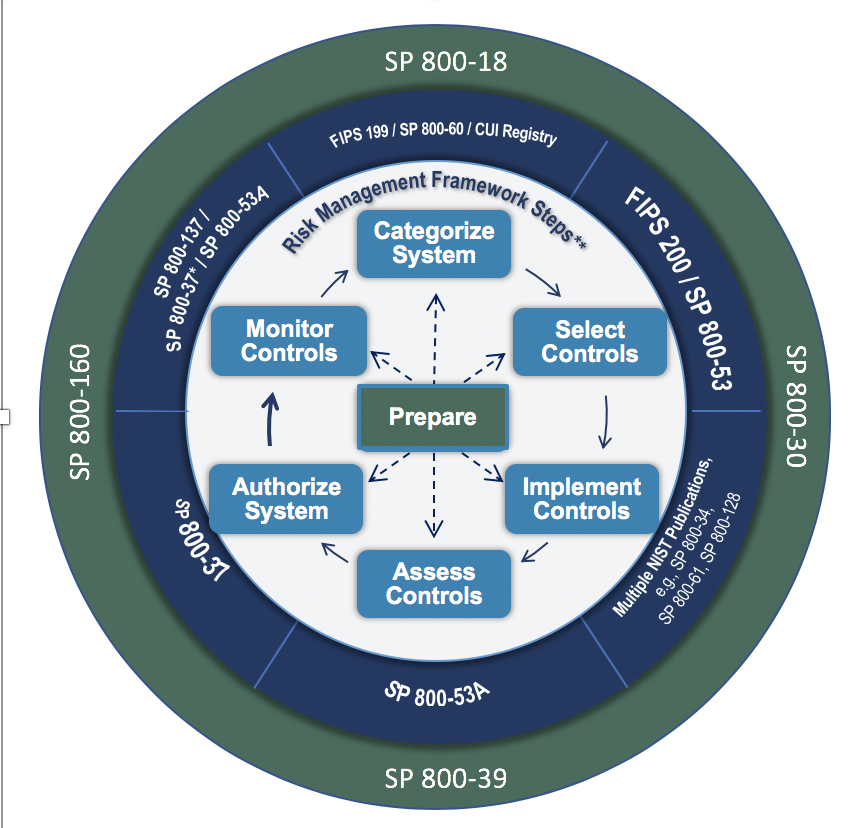
The RMF consists of seven distinct steps as described below:
- Prepare - Essential activities to prepare the organization to manage security and privacy risks
- Categorize - Categorize the system and information processed, stored, and transmitted based on an impact analysis
- Select - Select the set of NIST SP 800-53 controls to protect the system based on risk assessment(s)
- Implement - Implement the controls and document how controls are deployed
- Assess - Assess to determine if the controls are in place, operating as intended, and producing the desired results
- Authorize - Senior official makes a risk-based decision to authorize the system (to operate)
- Monitor - Continuously monitor control implementation and risks to the system
A graphic denoting these steps is shown in the picture below:
The remainder of this guide outlines how the modules and features within RegScale can be employed to effectively and efficiently implement the RMF within your organization.
Step 1: Prepare Step
The prepare step carries out essential activities for managing the RMF program. Within RegScale, this step can be performed using the following features:
- Stakeholders System - identify and define key management roles
- Users - establish user accounts and assign roles in the system based on each person's responsibilities
- Role-Based Access Control - limit access on a per record basis to enforce need to know
- Policy Module - define organizational risk strategy and tolerances along with continuous monitoring strategy
- Risk Register Module - conduct an organization-wide risk assessment (may also tie risks to Threats for Threat-based risk modeling)
- Catalogues/Security Controls Modules - load the applicable set of controls for your organization (includes all NIST catalogues but also other industry standards such as the Internal Standards Organization (ISO))
Step 2: Categorize Step
The categorize step informs RMF processes by determining impacts on Confidentiality, Integrity, and Availability (CIA) of systems. Within RegScale, this step can be performed using the following features:
- Security Plans and Components Modules - define system characteristics, categorization, and boundaries
- Classification System - define different classification types and stamp each record within the system to enforce consistent data labeling for sensitivity
- Workflow System - define steps to review and approve artifacts (NOTE: If electronic approvals are not allowed, then all artifacts in the system can be printed and routed for manual approval or converted to PDF for 3rd party digital signature applications (i.e. Docusign))
Step 3: Select Step
The Select step allows controls to be selected and tailored based on the risk to the system and its categorization. Within RegScale, this step can be performed using the following features:
- Profile Module - allows baselines of controls to be created and used to instantiate new security plans or components. Profiles consist of one or more security controls from one or more catalogues and can be precisely tailored as a baseline that can be applied to Security Plans and Components (NOTE: Profiles can also be applied to Projects, Supply Chain Contracts, and Projects)
- Assessments Module - build an audit plan to perform control monitoring over time either via automated means (RegScale Application Programming Interfaces (APIs) or pre-built integrations (i.e. Tenable Security Scanner or MITRE STIGs))
- Builder/Wizard Feature - auto-generate security plans and components templates from pre-built profiles
- Workflow System - define steps to review and approve artifacts (NOTE: If electronic approvals are not allowed, then all artifacts in the system can be printed and routed for manual approval or converted to PDF for 3rd party digital signature applications (i.e. Docusign))
Step 4: Implement Step
The Implement step defines how the controls are executed for the system and organization. Within RegScale, this step can be performed using the following features:
- Control Implementations Module - allows the customer to define the following for each control:
- Policy - what it is expected to do
- Implementation - how it does it
- Objectives - how the subcomponents of the control are implemented
- Parameters - how organization-defined elements were implemented for this system
- Status - overall state of the control (Fully, Partially, or Not Implemented)
- Quality - how repeatable and effective is the implementation
- Risk Mitigation - how each control mitigates a risk from the overall risk assessment
- Tests - how will you ensure the control is met for continuous monitoring
- Custom Fields - ability to build a custom form to collect any additional data not provided within the default RegScale configuration (NOTE: This feature is only for Enterprise Edition (EE) customers)
Step 5: Assess Step
This Assess step provides assurance that controls are implemented correctly, operating as intended, and producing the desired security/risk outcomes. Within RegScale, this step can be performed using the following features:
- Assessment Module - build out the assessment team, overall schedule, and discretely track each audit.
- Lightning Assessment Feature - establish a test plan and quickly conduct audits against the test criteria in our intuitive Graphical User Interface (GUI) with real-time compliance scoring
- Master Assessment Feature - group multiple control tests together to track overall progress in auditing the controls for continuous monitoring
- File Upload/Evidence Storage - provides a secure file storage mechanism with AES-256 encryption and MD5 hashing to store evidence of compliance
- Link System - stores links to remote repositories (i.e. SharePoint, OneDrive, Google Drive, etc.) where evidence may be stored to provide linking to audit evidence
- Time Travel System - provides cryptographically sealed version control system to show all changes to the record over time while providing high integrity that versions cannot be altered. This feature allows the customer to see exactly what changed on the record at any given point in time
- OSCAL Support - generate a Security Assessment Plan (SAP) and Security Assessment Report (SAR) on demand using our industry-leading support for the NIST Open Security Control Assessment Language (OSCAL) standard
- Issues/POAMs Module - document deficiencies and develop corrective actions to address non-compliances
- Kanban Feature - execute corrective actions in real-time in a collaborative setting using our drag and drop Kanban boards to track remediations
Step 6: Authorize Step
The Authorize step provides accountability by requiring a senior official to accept the security and residual risk of operating a system. Within RegScale, this step can be performed using the following features:
- OSCAL Support - allows generating the SSP and Components on demand for automated compliance checks in support of Continuos Authorization to Operate (ATO) processes
- Security Plans Module - generate security documentation on demand for Authorizing Official (AO) approval
- Risk Register Module - review residual risk after control mitigations
- Workflow System - define steps to review and approve system authorization
Step 7: Monitor Step
The Monitor step provides situational awareness about the ongoing security and risk posture of the system over time. Within RegScale, this step can be performed using the following features:
- Assessments - conduct manual assessment activities in bulk (with Master Assessments), quickly and repeatedly (with Lightning Assessments), or on-demand using the regular assessment module features
- Application Programming Interfaces (APIs) - develop automated scripts to perform compliance checks and log the results as automated assessments within RegScale
- Integrations - leverage our pre-built integrations to perform automated checks (i.e. with Tenable, STIGs, etc.) and auto-log tickets for remediation (i.e. in Jira or ServiceNow)
- Issues/POAMs - document any deficiencies and track remediation actions
- OSCAL Support - generate a Security Assessment Plan (SAP) and Security Assessment Report (SAR) on demand using our industry-leading support for the NIST Open Security Control Assessment Language (OSCAL) standard
- Dashboards/Analytics - review continuous monitoring results on our real-time dashbards or leverage our APIs to integrate external business intelligence reporting such as Microsoft PowerBI or Salesforce Tableau
- Workflow System - define steps to review and approve ongoing system authorization based on continuous monitoring results
Summary
The RegScale platform is purpose built to provide Continuous Compliance Automation for the NIST RMF to deliver a Continuous Authorization to Operate. By providing flexible modules and feautures for all steps, APIs for real-time monitoring and integration, and real-time dashboards for reporting and analytics, RegScale provides the most comprehensive and affordable solution on the market for RMF automation needs.
Updated about 2 years ago
