Security
Security Configuration
This page provides details on how to securely configure RegScale at multiple layers to provide a low risk, defense-in-depth posture.
- Secrets
- Secrets should be injected via Kubernetes Secrets or other run-time mechanisms such as environment variables or a Key Vault that are available when the container starts up
- For secrets that are entered via the RegScale Admin panel, all secrets are encrypted at rest with AES-256 (in addition to the SQL Server layer encryption)
- NOTE: For Enterprise customers (on-premise), all secrets are customer provided. RegScale does not store nor does it have access to client secrets. If these secrets are lost, they are irretrievable. RegScale only manages secrets for our Software as a Service (SaaS) offering.
- Database
- Enable Full Disk Encryption for SQL Server
- Ensure all traffic to SQL Server is encrypted using SSL/TLS
- Enable backups for Disaster Recovery
- Encryption at Rest
- All files are encrypted at rest using the AES-256 encryption key setup by the customer
- Each file is MD5 hashed and will not be served if the file has been changed outside of the system (i.e. ransomware)
- Encryption in Transit
- Customer is responsible for creating and updating SSL certificates to encrypt all web traffic to the browser or for any API calls
- Security Scanning
- To provide ease in security scanning, you can navigate to
https://yourdomain.com/login/scanto access the login screen with a disabled security banner to allow ease in scanning with 3rd party security tools
- To provide ease in security scanning, you can navigate to
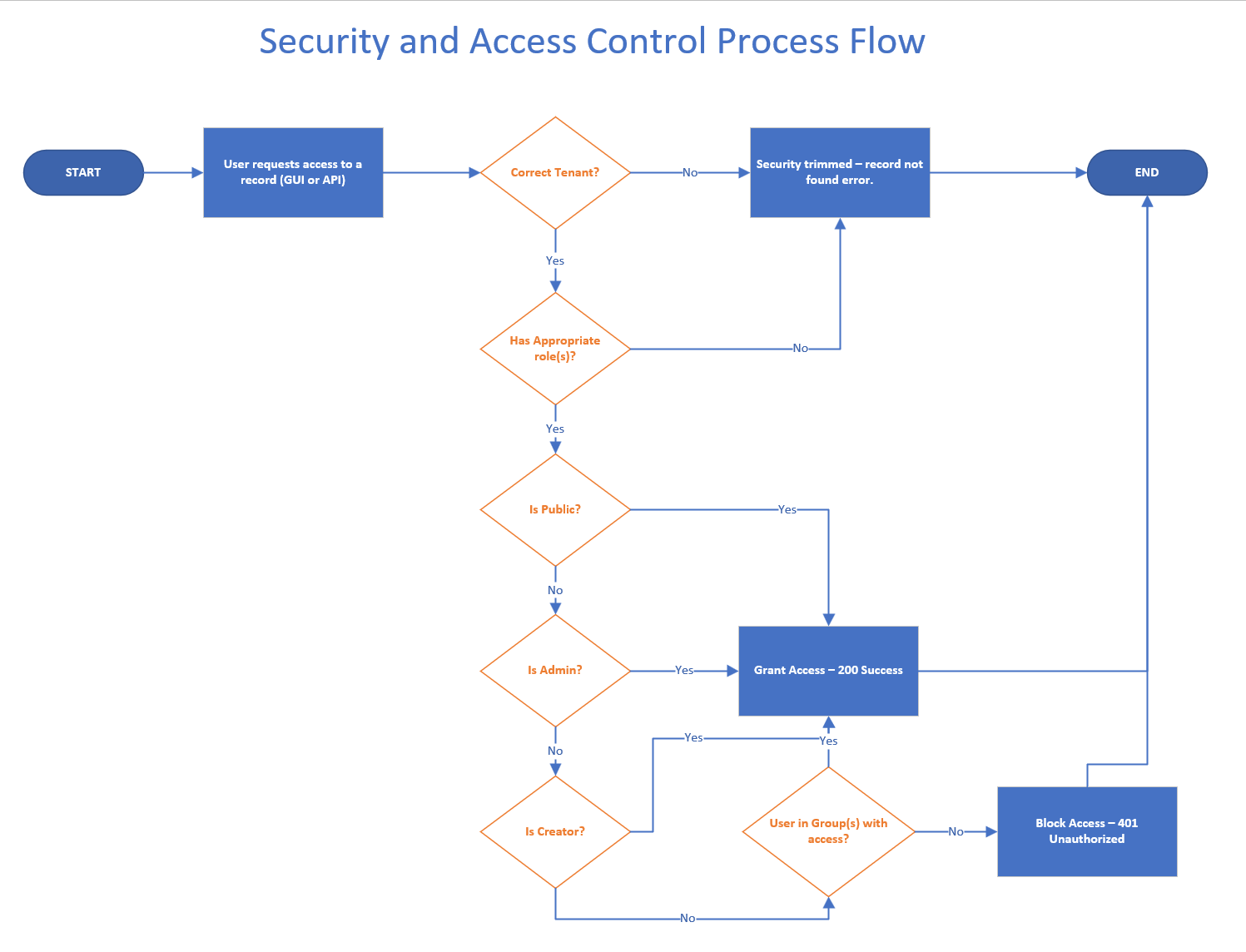
Layered Access Control
There are three primary layers of access control to protect RegScale data. The layers are as follows:
- Tenant Level - RegScale is a multi-tenant application and each user is assigned to a specific tenant. The user may only access data in their tenant and any other requests will be security trimmed where the data is not visible to the user.
- Role Level - RegScale consists of multiple roles and access can be controlled for each user based on need to know. For more info, see RegScale Users and Roles - https://regscale.readme.io/docs/users.
- Record Level - each record can also be specifically locked down to a specific group. The group will be assigned either Read/Write or Read-Only permissions.
A flow chart further describing this process is shown below:
Updated over 1 year ago
Did this page help you?
